 |
| Xiamen Art University Gate 2007 |
Certainly the mere continued existence of the great gate at the Art University of Xiamen helps define the security within its walls. There is a chair by the gate, but it is not occupied the day I was there. It was a beautiful day back in the northern summer of 2007, a day I had off, and I had taken the ferry over to Xiamen to see some of the older architectures. The Gate itself is like many others constructed of massive stone blocks, over which great tropical plants have grown. The inner surface of the gate shows two massive doors which close to create a very secure exterior when required. Locking people out, and locking people in, and preventing them from any kind of external attack.
That day I had been thinking over some of the developments we as control and safety system vendors might need to put into our SCADA control equipment. The western world had become much more aware that much of it's critical infrastructure was supervised by SCADA systems. We as vendors made two key components, the MTU and RTU, and we needed to address the need for heightened security.
Geographically based SCADA systems depend on telecommunications infrastructure on a grand scale for their minute by minute operation. Because of it's widespread nature, it is physically impossible to separate the telecommunication infrastructure from the public domain. This lack of physical protection and monitoring for the thousands of points of access to telecommunications used to manage critical infrastructure presents a set of security vulnerabilities which are difficult to quantify and even more difficult to manage. For the purpose of this blog entry we define all telecommunications infrastructure not belonging to the end user as 'public' with varying not accounted for levels of security.
The good news is that properly designed SCADA systems are resilient to communications interruptions. In other words, things keep operating if the communications fails, since the designs are arranged to cope with that failure. Many SCADA systems are designed with backup communications paths which are automatically switched in by their Master Stations should a failure be detected.
The bad news is that even properly designed SCADA systems are vulnerable to attack where the attack vector targets the 'public' telecommunications infrastructure.
Lets look at the old style telecommunications infrastructure used by SCADA. Much of the early work on communications was related to the use of telephone networks, since the technical infrastructure was created for the public, and since the 1930's SCADA functionality has been implemented using public telecommunications infrastructure. The speed has shifted from the 10 bits per second back in the 1930s to Internet speeds in 2010. For a good review of the use of telecoms in SCADA, you might refer to the paper by D.E Nordell. Communications Systems for Distribution Automation. The point is that SCADA has always depended on public telecommunications infrastructure, and whether this be a simple telephone line, or the Internet itself, it is almost by physical definition in the public domain.
 |
| Remote Terminal Unit [Foxboro SCD5200] |
Definitely the answer has to lie in our ability to secure the point at which control is effected. So lets start with the Remote Terminal Unit [RTU]. Lets confine our discussion to the requirements which relate to securing the RTU from attack by external means coming in through its many communications connections.
These days there are two ways RTUs communicate generally. One set of communications are done using Internet protocols [IP] and serial protocols [RS232, RS485, V11, V28]. RTUs accept supervisory commands via these connections as well as deliver reporting data over them, using well defined openly understood public protocols.
It really is like an open door or Gate to that pump station, lift station or other active part of the critical infrastructure. Keeping this door open is important to enable all the operational and maintenance people to do their day to day jobs. But equally important is the need to be able to shut the door when required.
If we go back to the University Gate analogy. The gate can be closed, but why close it ? We could say it is closed if there is a threat to anyone in the grounds. The security guards would come and close it. So detection of a threat is important, if we are to operate generally with the gate open.
Fortunately RTUs and MTUs the prime components of SCADA provided by control systems vendors, have an ability to monitor their own communications, as well as the state of controlled equipment in the field. The communications to RTUs are very periodic, and any interruption or change in the nature of these communications can be detected by the Master Station [MTU] as well as the Remote Terminal Unit [RTU].
Andy Oram's Beautiful Security : Leading Security Experts Explain... book has a set of chapters contributed by a number authors, which are well worth reading. The chapters dealing in particular with accountability and metrics. Since we don't have a lot of control over open protocols over relatively insecure public telecommunications infrastructure and in particular the Internet. These chapters should be of interest in the context of SCADA. Two key points which apply are:-
Accountability
It is very difficult to refute a possibly outrageous claim that your plant has been cyber-attacked if you cannot show some kind of evidence of that attack. How do you know ?. It would be nice for executives looking over their public infrastructure to be able to have a report which made their SCADA security effectiveness visible by some means of accountability. Accountability is the way in which Security can be assured. If I can count it, i.e. [number of attacks] or [number of intrusions] or [number of communications this minute] for example, then I can apply very simple metrics to that and determine the threat level of an impeding attack. Since potential attacks can arise from the public domain and into the relatively 'public' communications infrastructure, the points at which these can be monitored are the gates to the SCADA network.
Its really obvious or perhaps not - that you can determine a threat inside the gate, or outside the gate, or by monitoring who is passing through the gate.. depending on circumstances. The good thing in SCADA is that we know exactly what kind of traffic passes through the connection gates to the RTUs and MTUs. The messages that are sent are the same over and over and over and almost always come from the same source to the same destination.
If you are not monitoring for anomalies in the traffic flow in and out of the gate, you will not be accountable for security at the gate. So in order to be accountable, key traffic monitoring software at the RTU and MTU level is required. Who is connecting and why, and what messages are passing to and fro. Simply trending and alarming normal communications statistics can give an indication of a security breach in progress. If you are NOT monitoring traffic with a view to security, you can definitely NOT say whether a cyber attack has occurred or whether the pump just stopped due to normal failure rates.
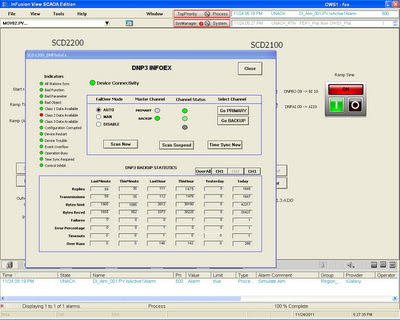 |
| Invensys SCADA comms information on a DNP channel |
So - given we can make RTUs as gates accountable - it's easy enough - they can count things, and they can keep track of events with inbuilt event buffers. And given we can make MTUs accountable - they can count communications, keep statistics, in their own historians and event buffers. The pic at the right shows a typical monitoring screen to show the engineer how the communications are monitored by the system.
In addition to normal good practice with IT, it should be possible to make the SCADA communications network 'security aware' by providing high quality accountability of communications and better metrics and KPI's for normal communications over the public telecommunications infrastructure.



No comments:
Post a Comment